clean up docker networks/interfaces
docker network ls
then
docker network rm networkname
docker network ls
then
docker network rm networkname
昨天才注意到我的 racknerd vps被墙了。换一个IP要 $3,虽然不贵,但racknerd并不能保证新IP是没有被墙的。 网上东搜西搜,有人建议用 cloudflare CDN 挽救,但这样只能解决一个端口(即443),无法享受到 kcptun 加速的快乐。
还有其他的法子吗?我想到了Tailscale。如果你身在墙内,由于VPS IP已经被墙,你无法直接连接。但你可以用 azure cloud terminal 或者其他云服务商提供的 cloud terminal,因为他们的云Shell到你的vps通常都是通的。
我很懒惰,下面简要罗列主要步骤:
这样当然是有局限性的啦,除非你利用openwrt得到一个无墙的wifi,你每个设备都要安装tailscale。这也不是什么坏事,tailscale这个利器,早装早享受。说不准啥时候就能救你一次!
I recently signed a new broadband contract with One NZ and received a HUAWEI DN8245X6-10 wifi router. This new router offers WIFI6 connection, which is faster than the Vodafone UltraHub. Unfortunately, I was unable to get port forwarding to work on this router, which was quite frustrating. Even One NZ's customer support couldn't assist me, as they admitted to not having training on port forwarding support. However, they did provide me with some useful information - One NZ doesn't block any ports, and the old Vodafone Ultrahub can also support the cable modem. This gave me some hope. I decided to use the Vodafone Ultrahub as the main router and DN8245 as a secondary WIFI router. After spending a few hours on it this afternoon, I finally made it work. Here are the key steps.
Connect the Ultrahub's WAN port to the cable modem. I didn't change any settings; it simply works. I was happy to find that the port map settings work with this new HFC broadband as well!
Connect the DN8245X6-10's WAN port to one of the LAN ports of the Ultrahub.
Go to http://192.168.1.1/ and log in to the router using "admin" as the username and the password printed on the router. 
Go to Advanced => Wan.
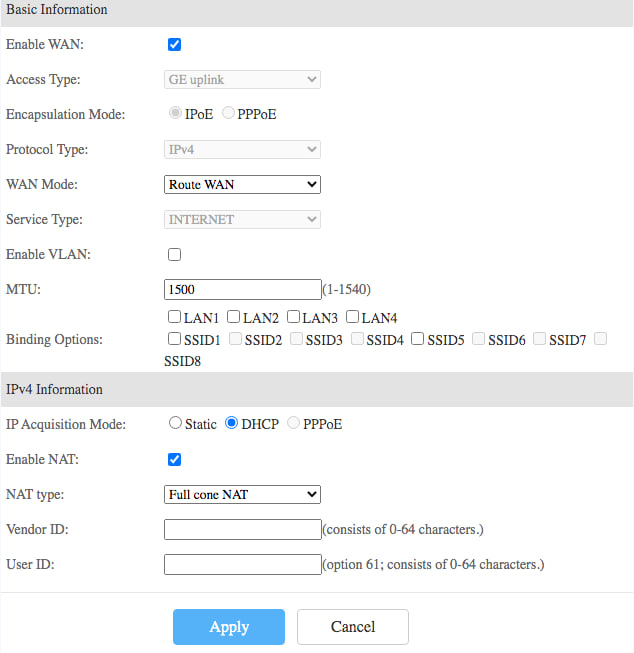
Go to Route => IPV4 default route. (I spent at two hours before I found this step is critical)
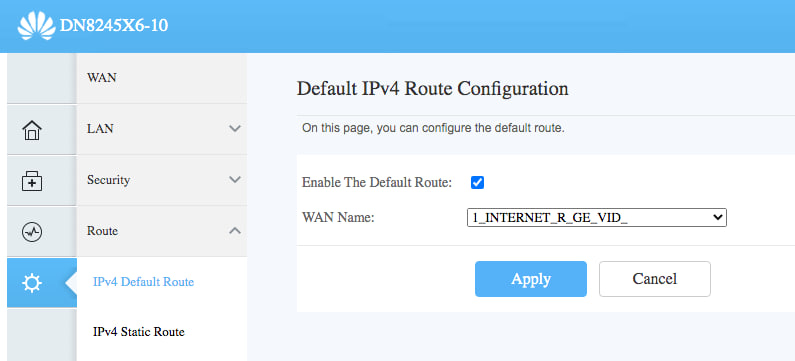
And, that's all! BTW, don't waste your time to try to set a bridge wan. It simply doesn't work:cannot get an IP from master router for unknown reason.
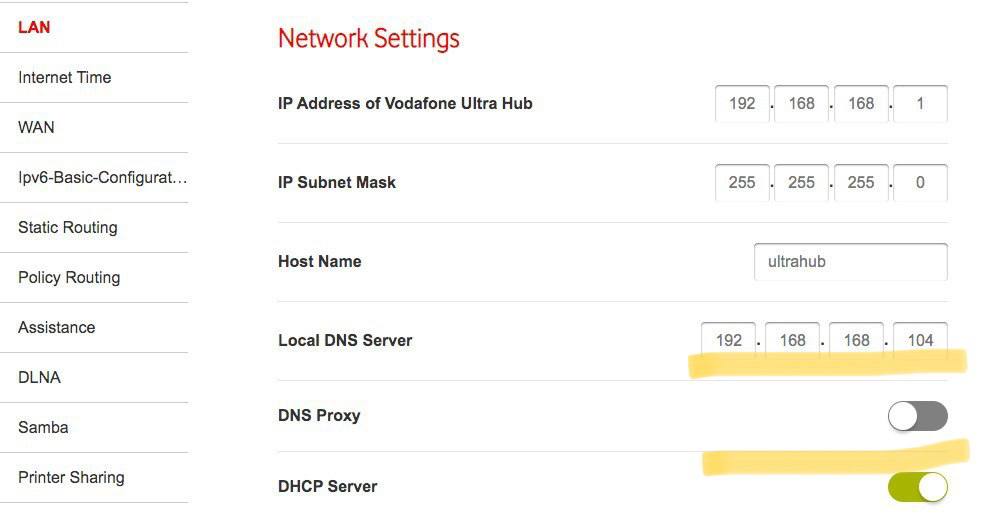
The key is to tick off the DNS Proxy switch, otherwise, DNS clients won't obtain the local DNS value as their DNS.
半年多前配过一次,磕磕绊绊的,勉强配好了能用。这次老朋友又买了一台类似的机器,我以为会很快搞定,结果又陆续整了好几个小时。为避免下次折腾的时候浪费时间,简要记录一下折腾过程。
回头看看也没什么.....就这么点事儿,整了几个小时。如果第一次整完就写篇备忘记录....哈,亡羊补牢,犹未晚,我这不就写了么!